Introduction to Phishing
Phishing has become one of the most prevalent forms of cybercrime in the digital age. This malicious tactic involves deceiving individuals into providing sensitive information such as usernames, passwords, and credit card numbers by masquerading as a trustworthy entity. Understanding phishing is crucial for users to safeguard their personal data and avoid falling victim to these scams.
How Phishing Works
Phishing attacks typically employ deceptive emails, messages, or websites that appear legitimate. For instance, a common method involves sending an email that looks as though it is from a reputable organisation, such as a bank or social media platform, asking the recipient to verify their account information. These phishing emails often contain urgent calls to action, encouraging immediate response.
According to the Anti-Phishing Working Group (APWG), the number of phishing attacks has surged significantly in recent years, with a notable increase in sophisticated techniques like spear phishing, which targets specific individuals or companies, making them more difficult to identify as scams. In the first quarter of 2023, the APWG reported over 1.5 million phishing attacks, marking a 20% increase from the previous year.
Types of Phishing Attacks
Phishing can manifest in various forms, including:
- Email Phishing: This is the most common form where attackers send fraudulent emails to a broad audience to trick them into revealing personal information.
- SMS Phishing (Smishing): Scammers use text messages to deceive individuals into responding with sensitive data.
- Voice Phishing (Vishing): Voice calls are made to impersonate legitimate sources, attempting to extract personal information.
- Website Phishing: Attackers create fraudulent websites to closely resemble legitimate ones, where users can inadvertently enter sensitive data.
Preventing Phishing Attacks
To protect against phishing, individuals should follow several best practices:
- Be cautious with unsolicited emails or messages, especially those requesting personal information.
- Verify the authenticity of requests by contacting organisations directly, rather than responding through provided links.
- Use security features like two-factor authentication (2FA) wherever possible.
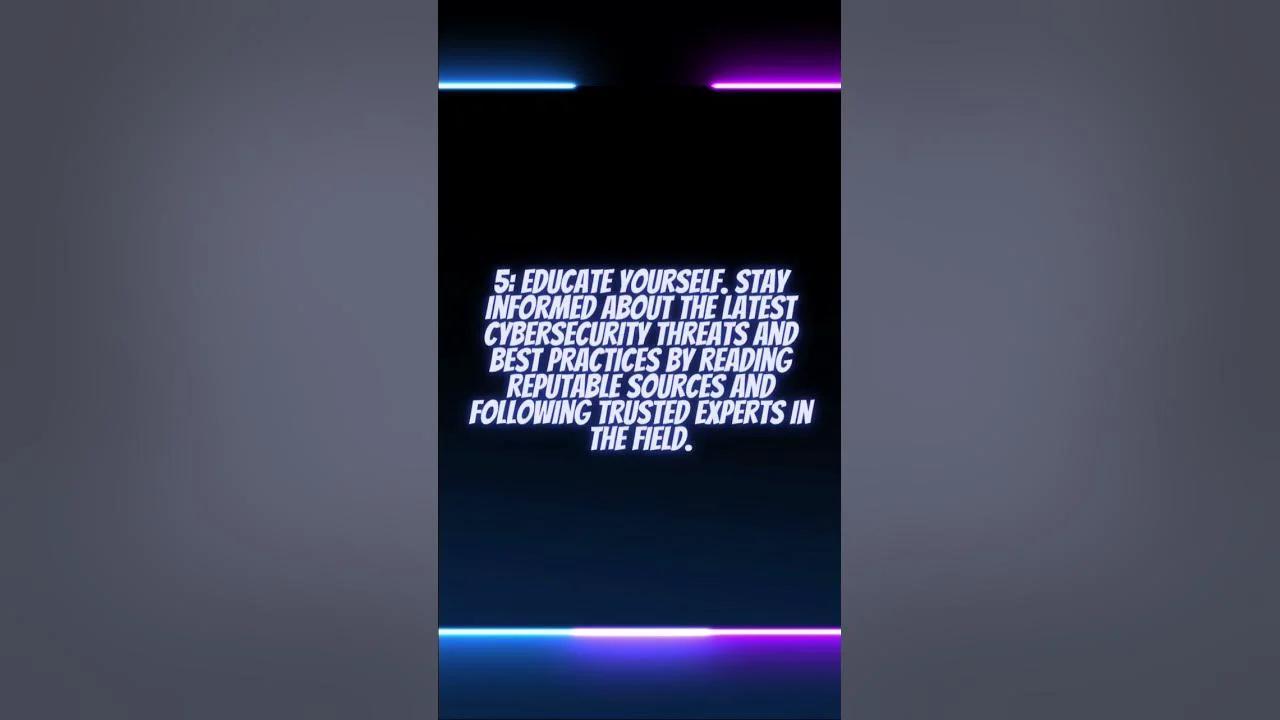
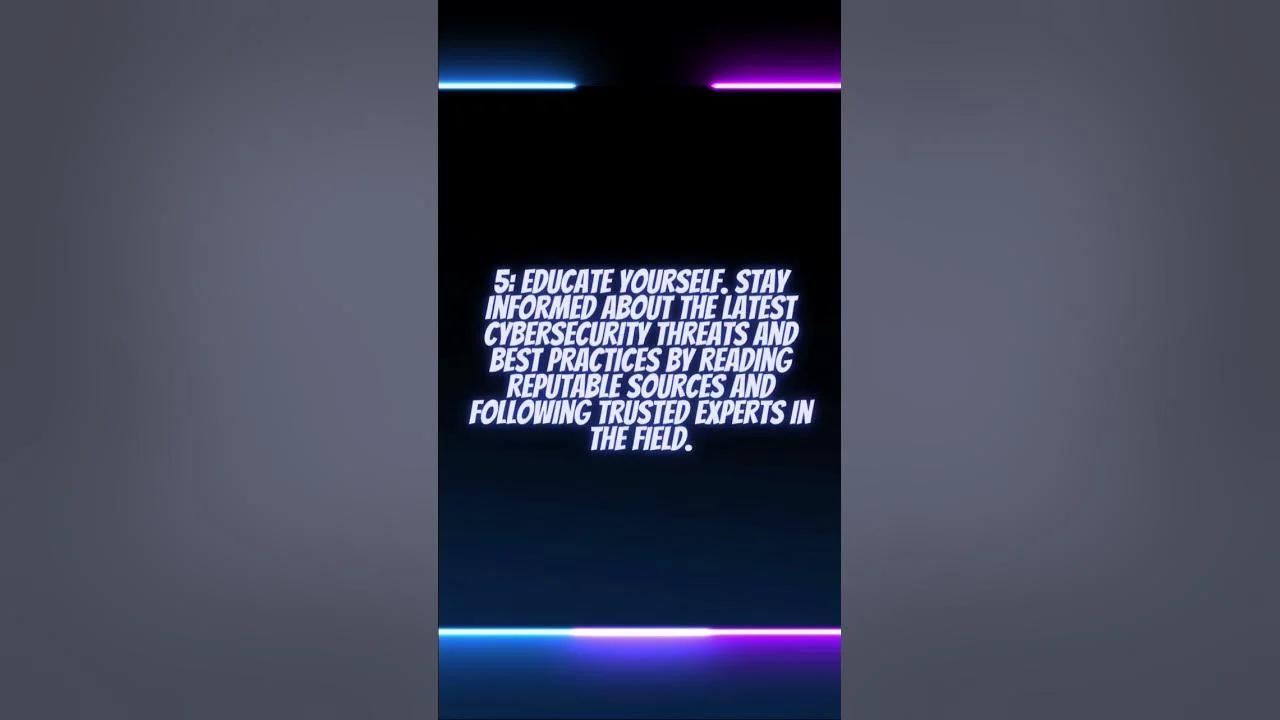
- Educate yourself and others about recognizing the signs of phishing.
Conclusion
Phishing represents a significant threat in today’s digital landscape, posing risks to identity and financial security. As cybercriminals continue to refine their techniques, awareness and education remain paramount for users. By understanding what phishing is and how to recognize it, individuals can take proactive steps to protect themselves and their private information from potential threats. As technology evolves, so will the tactics employed by phishers, making it essential for users to stay informed and vigilant.